Why Choose ThreatDown?
Unlike bloated, complex security platforms, ThreatDown delivers serious protection without the heavy lift.
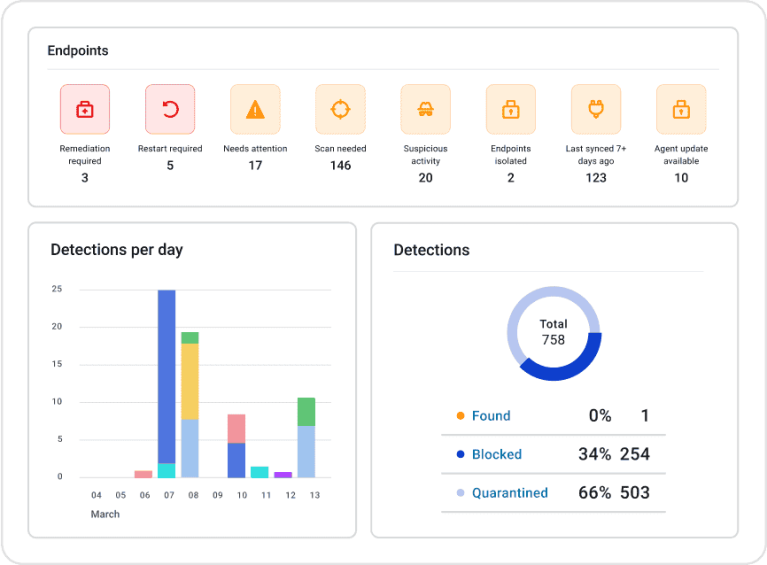
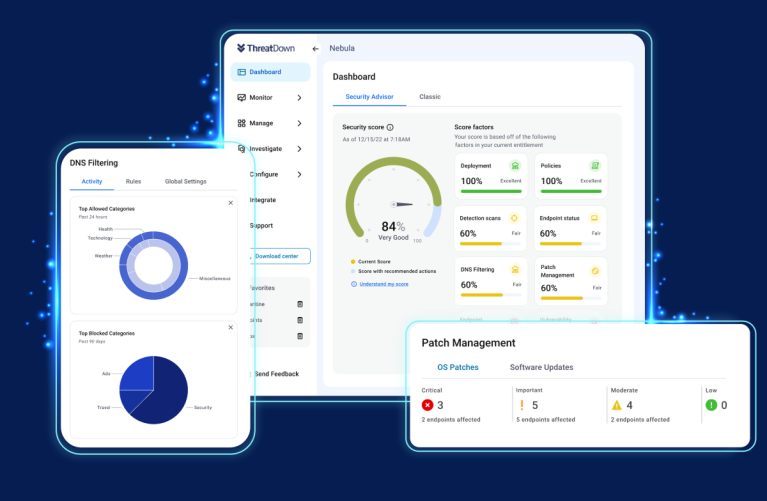
- Simplifies endpoint security with intuitive dashboards.
- Reduces IT costs by automating patching & remediation.
- Protects anywhere – Windows, macOS, iOS, Android, servers, cloud workloads.
- Trusted by thousands of IT leaders, MSPs, and SMBs worldwide.