SecurEnvoy’s Passwordless MFA: A Game-Changer for Identity Protection
SecurEnvoy’s passwordless multi-factor authentication (MFA) is revolutionizing identity protection in 2025—enhancing security while improving user experience.
Why SecurEnvoy’s Passwordless MFA Is a Game-Changer for Identity Security
Passwords remain the leading cause of security breaches, vulnerable to phishing, credential theft, and human error. In today’s cloud-based, hybrid work environments, identity is the new perimeter—and passwords can’t keep up.
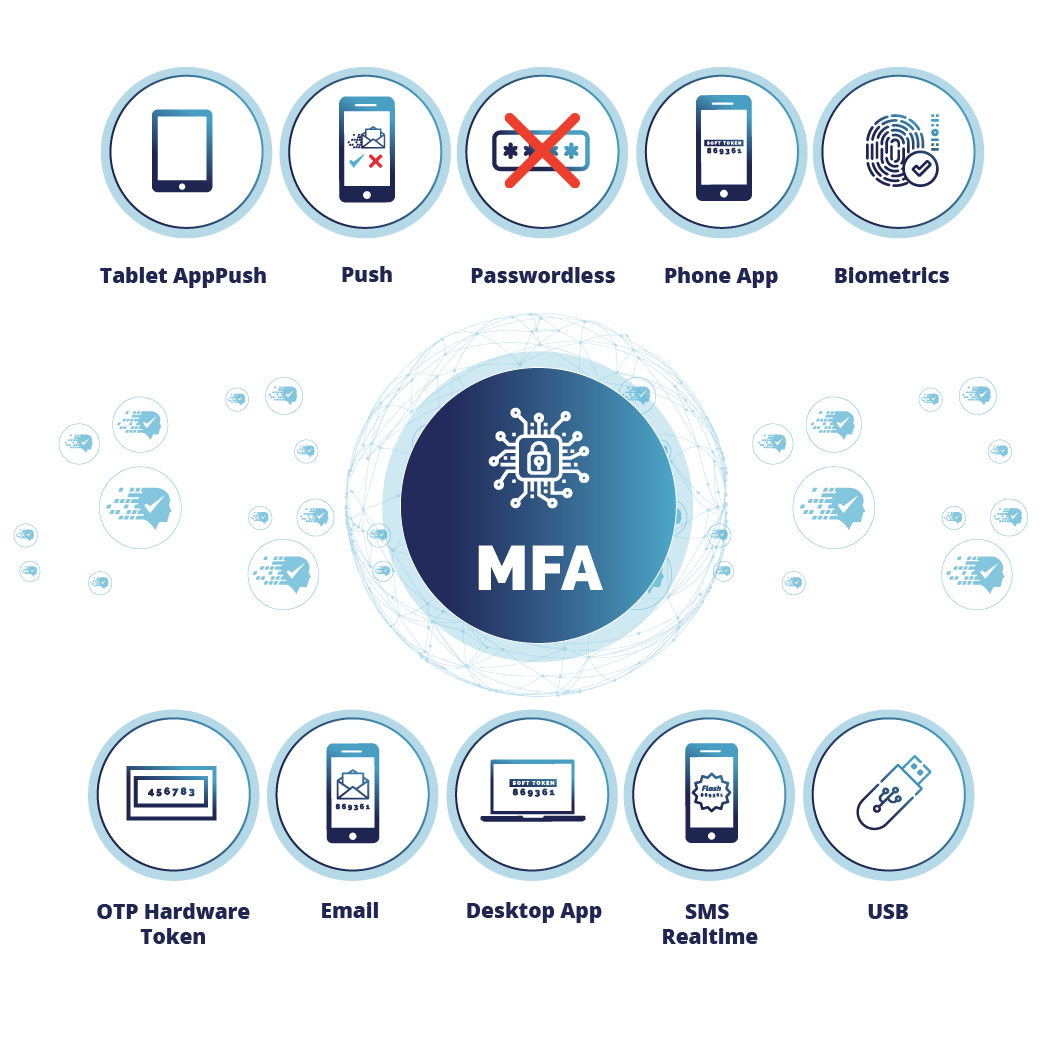
SecurEnvoy’s passwordless MFA replaces passwords entirely with biometrics, push authentication, and device trust, delivering stronger security and a seamless user experience. It prevents phishing, cuts reset costs, and supports Zero Trust and compliance frameworks like NIST, GDPR, and HIPAA.
Flexible and integration-ready, SecurEnvoy works across cloud, on-prem, or hybrid setups—making it ideal for industries like finance, healthcare, education, and government. Passwordless isn’t a trend—it’s a smarter, safer way to secure access.
Every password is a liability waiting to be exploited. The future of security begins when we let them go
Conclusion
The Future is Passwordless—And It’s Here Now
The days of relying on passwords as the first—and often only—line of defense are behind us. As cyber threats grow more sophisticated and identity becomes the primary attack surface, clinging to outdated authentication models is a risk most organizations can no longer afford.
SecurEnvoy’s passwordless MFA represents a critical evolution in identity protection: eliminating the vulnerabilities of passwords while enhancing security, usability, and compliance. It’s not just a more secure login method—it’s a strategic move toward Zero Trust, simplified user access, and reduced operational friction.
Whether you’re securing remote teams, protecting sensitive data, or preparing for modern compliance demands, passwordless MFA provides the control and confidence needed to move forward securely.